Public Key Cryptography
The following is a visual representation of public key cryptography being used for encryption, signing, validation, and decryption, in that order.
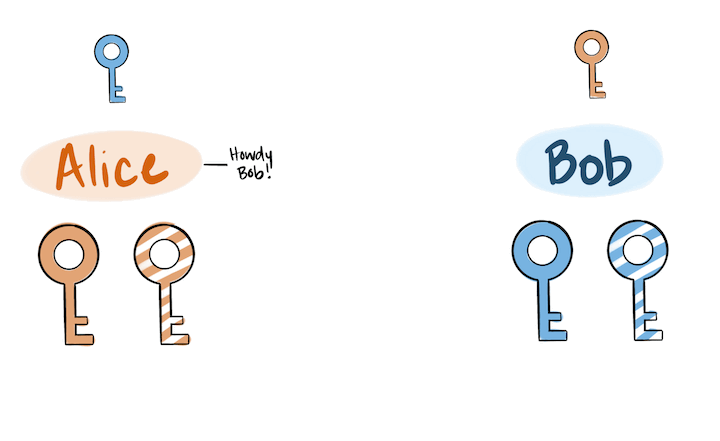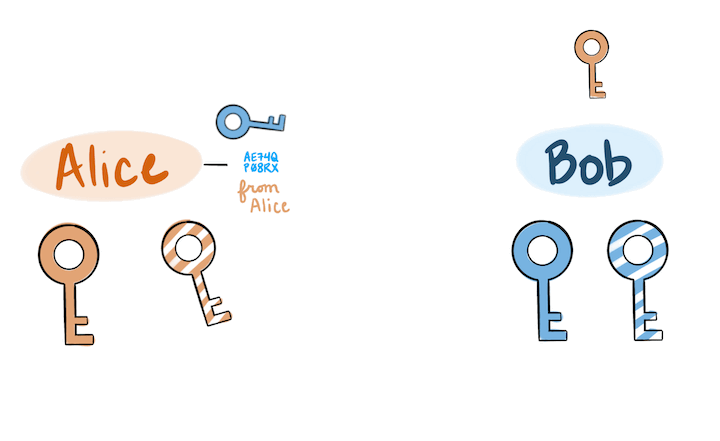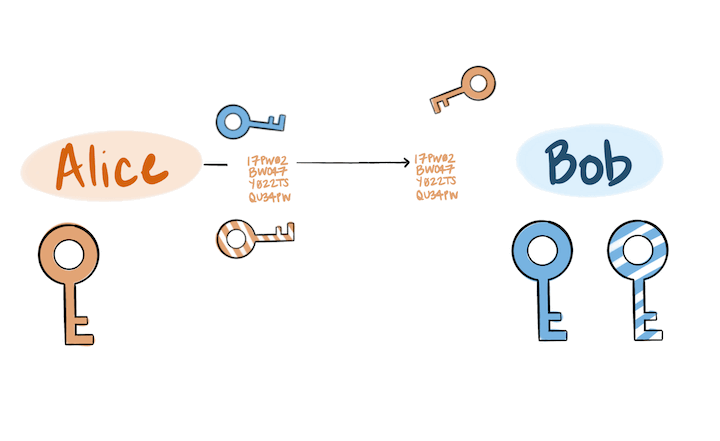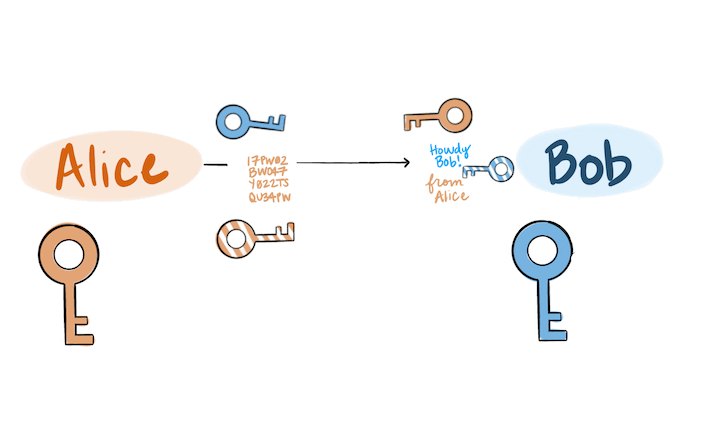
The following is a visual representation of public key cryptography being used for encryption, signing, validation, and decryption, in that order.
